It’s funny, whenever I hear that I have flashbacks to someone getting ready to tell me I’m in trouble for something. No, I’m not going to tell you you’re in trouble, but I do feel we’re reaching a point where the pace of new features, technologies, and capabilities is quickly outpacing the ability of IAM and security teams to respond. So, as I said, we need to have a chat about who is responsible for Identity, and who is responsible for Security.
I’ve had countless conversations with CISOs, Identity leaders, and business leaders this year around their identity programs and capabilities. One common thread I am hearing is how they building out Identity programs to support AI in their environments. Whether it is business, customer, or partner use, all have the same question. How can we scale, protect, and serve our business at an evolving scale not usually seen in technology changes?
To take a step back for a second, I’ve talked about it (and a few others in my network like @Steve Tout at Identient), and written a few papers, on the evolving and maturing Chief Identity Officer (CiDO pronounced ‘cheeto’) role of organizations. Where this sits is at the intersection of the Business, People Management, Security, and Technology (see below). The responsibility of the CiDO is to define, build, and run the Identity Program for the organization serving the main consumers of Identity, e.g. Business, People, Technology, and Security.
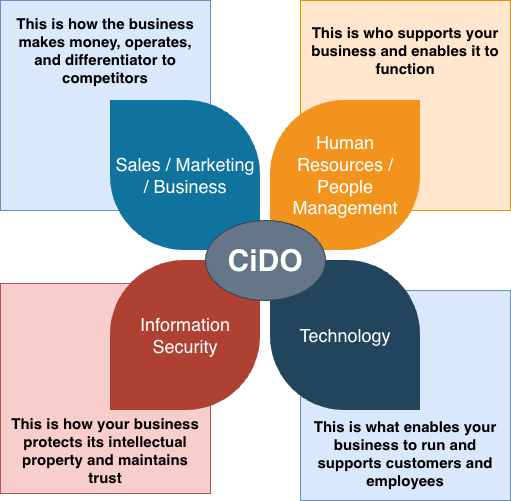
In the current setup, this is usually fulfilled by an Identity Director or similar sitting in the security organization ultimately reporting up to the CISO. The challenge with this setup is by the time the Identity leadership gets involved, this is a security project and coming in after other requirements may / have been defined. Or, what I encounter too much, this security requirements have already been defined, and Identity is left with implementing what it can to support the security requirements, not the business or technology need.
But this is the challenge, how, or what driver, is going to shift this need to make the CiDO a reality? The answer is presenting itself now in the explosion of identities needed to run the modern organization and support the myriads of AI use cases. No more are we just focused on users and service accounts, now we have Users, the delegated Agentic Identities, Agents, models, service accounts, and an exploding list of support infrastructure non-human identities. On top of that, all this is fighting for bandwidth on an ever-aging Identity infrastructure built to support a different use case.
What’s Blocking This Move?
I’ve been asked this multiple times but had a conversation recently that really focused my thought process on why this has not caught on, and possibly how this is going to shift. There are several primary reasons why this is moving so slow which includes:
- Established Roles and Responsibilities Supported by Compliance Frameworks: You read any established organization structures, policies, or requirements and they generally include Identity in the Security organization. So, naturally, this has become a Security problem. Whether it is Identity Governance, Multi-factor authentication, or authorization, this generally manifests itself as a security requirement, thus is provided in the Security organization.
- Budgets: Most Identity projects, due to roles and responsibilities in organizations, are part of the Security budget competing for other needs and wants.
- Maturity of leadership: This is a hard one. I’ve been in the industry long enough that I’ve been able to experience (as an engineer, architect, and CISO myself) the identification, need, and maturing of the CISO role. This took 10-15 years (at least) from inception to really becoming a board level position with visibility in organizations. Identity being an evolving technology, albeit established philosophically, is still maturing and growing and established leaders in the space are still bubbling to the top of the organizational visibility.
Why Now? What’s Changing?
The short answer to this question, we’re being asked to do more with the same number of resources and budgets. Security organizations are faced with an increasing need for specialized skills for things like SecOps and Endpoint protection, while the foundational technology (Identity) is staying stagnated. As the latest Artico / IANS CISO benchmark shows (https://www.iansresearch.com/resources/all-blogs/post/security-blog/2025/08/14/what-are-the-top-security-budget-spend-priorities), IAM accounts for ~10% of security budgets while the remaining 90% is allocated for traditional security spend. While this number may be increasing based on the results, it is being outpaced by business and Security needs for IAM in organizations.
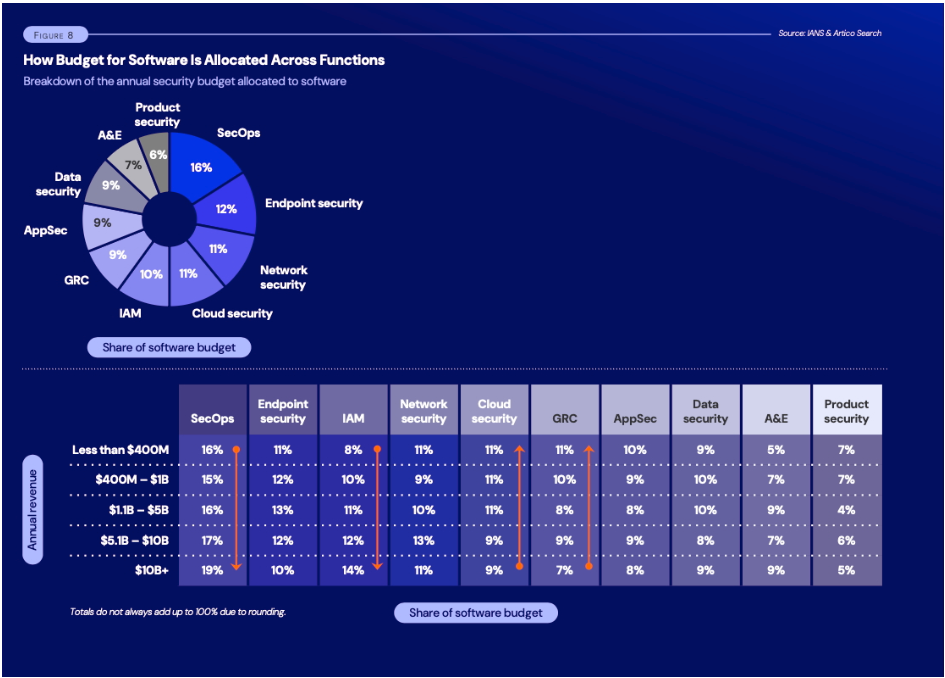
The harder answer to this question is looking at everything else competing with Identity. In a CISO daily standup or dashboard, Identity is 1/10th the focus based on the above research, but touches ~75-80% or the need. You look at Endpoint, Network, AppSec, Data Security, all have Identity requirements and needs. How do you define who should have access, or implement your Zero Trust initiatives, without a solid Identity Foundation? And this is not even looking at the business, technology, or people needs for Identity. The short answer here is Security cannot keep focusing on everything while maintaining adequate coverage and capabilities.
How Would This be Structured?
I get a lot of pushbacks when I start bringing this up, but if Identity is not a Security function, where does it live? Well, it is a standalone organization like it shows above that has dotted lines to all its consumers: Security, Technology, Business, and People. In this new model, the paradigm and roles shift on how Identity is defined and served in the organization. Let’s use AI since is top of mind as an example here on how this would be structured.
- Security: CISO / Security organization defines the requirements on how AI should be secured. They define the guardrails, policies, etc. that should be put in place, and in some cases implement the infrastructure needed for it (e.g. AI gateways). But, for Identity, they define who needs to be authenticated and authorized, not how it is done.
- Technology: They define the need for the AI infrastructure services. They need model discovery, services, and integrations and who the consumers are.
- Business: They define the use cases for AI and how it is going to be used by customers, and applications.
- People Management: They define the requirements for how this is going to improve people’s abilities, who should have access to what (roles / rbac) and appropriate organizational people controls to be defined.
- CiDO: defines IAM infrastructure that meets the requirements of all the consumers and best way to serve each group while meeting the organizational demands.
This would be modeled like the below. But at a high level, each consumer plays a part in defining their requirements and use cases. All this is normalized by the CiDO into a working model of how the Identity services will be built, and run, to serve the organizational needs.
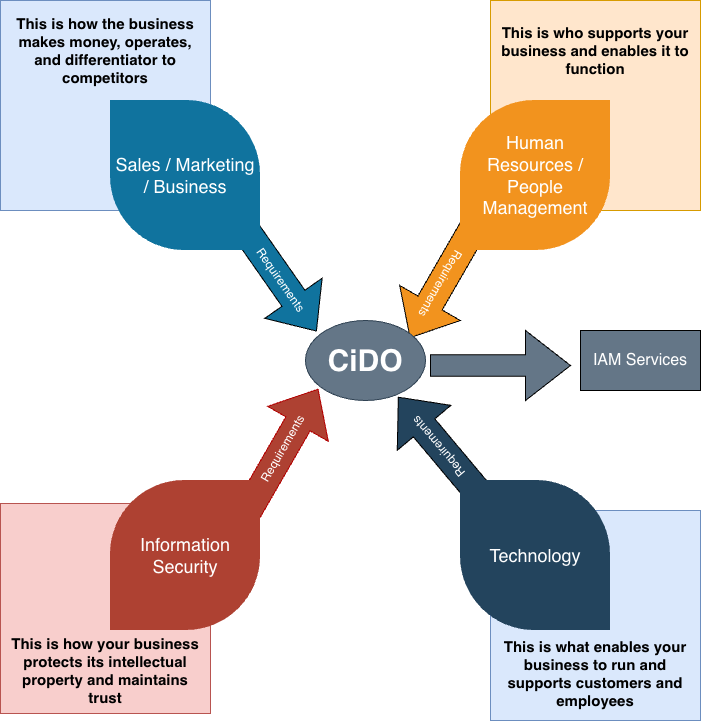
The benefit of this is organizations now have a strategic capability to define the requirements and use cases, and a leadership structure and organization to build and run the infrastructure to meet those needs. Given Identity is at the center (no pun, or maybe a little pun intended to the Identity at the Center podcast (https://www.identityatthecenter.com/)) of most things in the modern organization, this builds scalable, and inclusive, identity services meeting all requirements.
Additionally, Security teams can re-allocate focus on defining requirements and needs to protect organizations, not being responsible for building and running it also. While 10% may not be a lot of extra bandwidth, it all helps given the threats and challenges we face in the modern Security climate.
Closing Thoughts
I know this won’t happen overnight, and the security side of me has concerns with Identity being a separate organization given its criticality to Security, but I believe we are at or beyond the tipping point of Identity being more than just Security. And believe Identity will start slipping given all the demands on modern Security organizations. This should be function, experience, services, and Security better aligning with everything Identity can do for an organization.





