Three months ago, I made the decision that after working for others for 24+ years, it was time for me to start charting my own path. Two months ago, I made it happen. Not because I was dissatisfied or didn’t like what I was doing, just felt it was time to be my own boss. I can honestly say this was one of the best decisions I have made in my career and have loved every minute of being on my own. Yeah, I miss my old team and co-workers, but I am enjoying the creative freedom to be able to think and share my experience. I don’t think I could have done this when I was younger since I really was more in reactive work mode, but with experience has come the desire to start contributing more.
A lot of friends and co-workers have asked why now, and what has changed to make me feel this way now? I don’t think I can pinpoint an idea of why now, but I do have a driving force and mission for the CidO (Chief Identity Officer) and HATSec. That mission is to start rethinking IAM and how we view it internally and externally to organizations.
I have been doing Security for 24+ years, fifteen of those specifically on Identity and Access Management (IAM). On top of that, even though IAM is a relative young field, I am doing a lot of the same types of things I was doing 15 years ago (authentication, SSO, user provisioning and governance, etc.) just with different drivers, technology behind them. Same requirements, same outcomes, 15 years later. Yeah, I have had success over the years, and helped and built a lot of cool things, but is a lot of the same.
So, when I started looking at going out on my own, I really asked the question of myself, as to why. If I am doing the same thing I was doing 15 years ago, just different vendor / technology, have I really helped or made a difference, and if not, how do I start making a difference? Where are the gaps in IAM and how do I enable change (through technology, knowledge, people)?
It took me a little while to figure this out for myself and take a broader look at what I was doing to come to the conclusion we, as an industry, are looking at the IAM in the wrong lens. Over the years, IAM has become a security solution for more organizations. Meaning, it is architected, managed, and communicated from a security perspective. But, IAM is not a security solution or problem, it’s a people problem (and non-Human depending on how you look at it). Me being security first person (given this is my education and background) find it hard to say this, but over the years IAM has grown beyond just a risk & compliance tool, to be a business enabler. So, if we are going to really enact change, we need to start looking beyond Security for IAM and looking at it as a standalone strategic organization and process.
So, my ‘why’ for starting HATSec and the From the CIdO series is documenting how we make this happen.
To start, since we know we need to rethink this, we need to start looking at how we organizationally align IAM. Most organizations I have ever worked with have IAM as a team at least 2-3 levels deep under the Security team / structure. Scary still, some I have talked with that are just starting still have it as the ‘Active Directory’ group (sorry anyone that still has this, not poking fun). So, we have a strategic technology that can shape organization processes, people, differentiate sales, and help enable compliance under the Security organization structure?
To change this, we need to establish separate, standalone leadership structure (hence the Chief Identity Officer) for IAM under the COO, CEO, or similar much like technology and security do today. This will establish IAM as a standalone function serving four main organizations of the business (see below).
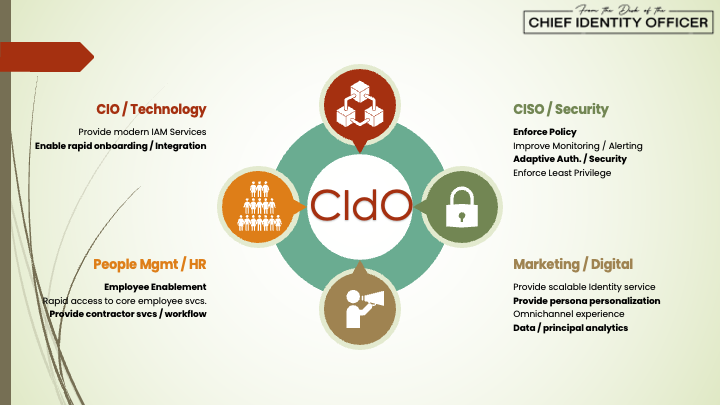
In this model, we have the CIdO as a standalone role, with budget and strategy, serving the four groups:
- Technology (CIO) – Everything any more is going to have a cloud, personalization, or access requirement. Additionally, developers are distributed across services, locations, and all need to be able to perform their job quickly. IAM serves this purpose.
- Security (CISO) – Security is still going to have a big IAM component when it comes to defining, maintaining, and ensuring protection of digital assets. But, security should not be running IAM, they should be contributor to defining IAM requirements with execution elsewhere.
- Marketing / Sales (CDO, CMO) – A lot of marketing and sales folks I talk to want to personalize their applications, be able to understand the who, what, where data from their applications to build better experiences, but have never viewed IAM as the tool that can enable that. The CIdO need to understand how the business operates in their digital, sales, and partner channels so they can better enable these functions to help drive business growth.
- People Management / HR – I now see organizations hiring and curating Chief People Officers with the role of building and enabling employees to contribute to the organization. One of the biggest inhibitors of this when talking to these groups, is lack of access, understanding, challenges with talent management, hiring, onboarding, etc. Talking to employees and reading some of the Best Places to Work surveys, you see some of the biggest complaints is around lack of access, not knowing how to request things, overburdened with processes, etc. These are all, or can be enabled, by strong IAM processes and technology.
I agree, this is not going to happen overnight. Like I said, I have been going down the same track doing Access, Governance, Privilege, etc. for the last 15 or so years, and know people that have been doing it longer than me. Additionally, most IAM vendors brand, market, and sell to the security needs of organizations. But, at some point, for IAM to become that differentiator for the rest of the organization (see above), it needs to establish its own identity (no pun intended).
Going forward, this is my drive, passion, and why. I’ve already submitted a couple talks for RSAC 2025 around this (anyone from the selection committee please choose me!), will be doing some webinars talking about the Chief Identity Officer roles, and am looking forward to chatting with everyone more.
You want to debate me on this, would love to set something up with my CISO friends on the merits of IAM not being a security tool, but a collaborative organization. Reach out and let’s set something up to debate.
From the CIdO, it’s time to start making a change, and it starts with us.






One Response
Cido role applicable for large organizations, not for small and medium size.